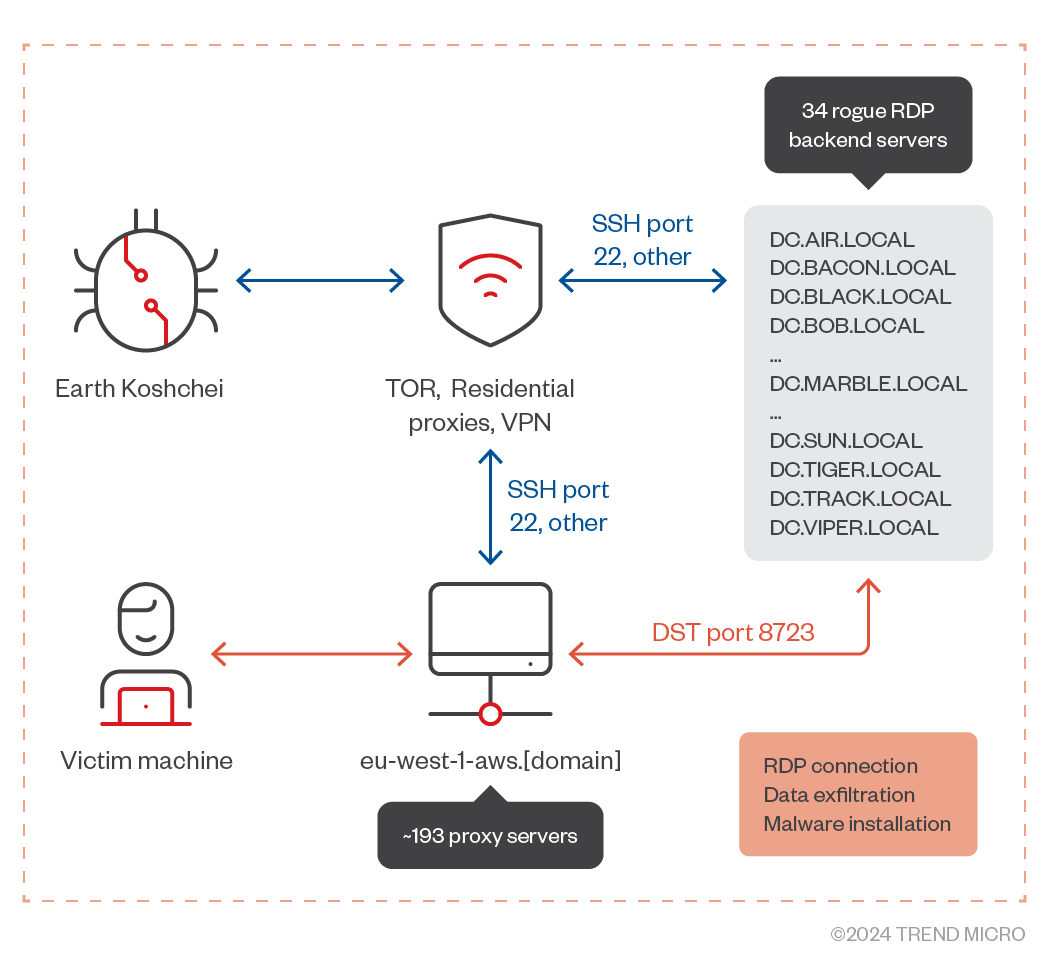
In October 2024, the Russia-linked cyber espionage group APT29 (aka Earth Koshchei, SVR group, Cozy Bear, Nobelium, BlueBravo, Midnight Blizzard, and The Dukes) used rogue RDP attacks via phishing emails targeting governments, think tanks, and Ukrainian entities to steal data and install malware. The threat actors used spear-phishing emails to trick recipients into using a rogue RDP configuration file, causing their machines to connect to one of the 193 RDP relays operated by the APT. The attack technique employed in the campaign was described in 2022 by Mike Felch, it involves the use of a MITM proxy and the PyRDP tool to minimize suspicion and reduce user interaction during a rogue RDP attack.
Author: Pierluigi Paganini
Published at: 2024-12-18 22:24:52
Still want to read the full version? Full article