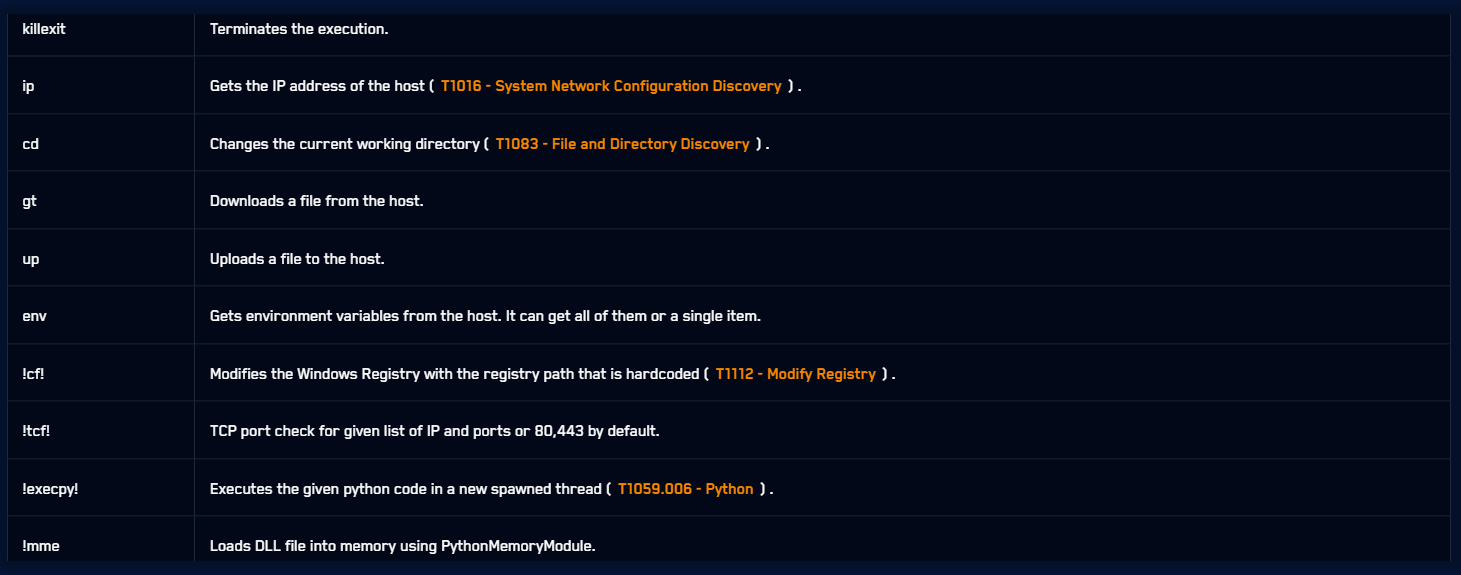
Some variants execute the obfuscated payload immediately after writing it to disk, while others load the payload and call a specific function from it.” reads the report published by cybersecurity firm PRODAFT. The researchers noted that a Python script with ~30 lines serves as the main entry point, decrypting and executing the real payload. To determine the local IP, it creates a UDP socket to 8.8.8.8 on port 80, letting the OS resolve the appropriate address without actual traffic.
Author: Pierluigi Paganini
Published at: 2025-04-02 21:38:24
Still want to read the full version? Full article